Securing Web API with user authentication and token authorization using custom database
WebAPI Security,
which is most widely popular and needed feature for every developer who is working
on services for their client devices. You might have seen many topics on API
security over the web but many of them misleading you the actual point where
authenticating your users against custom database, issuing a token, authorizing
the requests against the issued token and providing the way to generate the
refresh token.
Secure API Methods:
We are going to discuss on below points to fulfil our need
on API security in ASP.NET MVC.
- OWIN Setup
- User Authentication
- Token Generation
- Refresh Token Generation
- Secure API Methods
The affected areas for your project are as shown below. You
might not have the providers now, but you will be end up creating them while
going through the topic.
OWIN Setup:
Microsoft OWIN provides the core features of security for
your Web API, which includes the token generation and authorization.
Before you start anything in API security, install the below
packages using Package Manager Console or NuGet Package Manager from your
Visual Studio in case if you don’t have them now.
- Microsoft.AspNet.WebApi.Owin
- Microsoft.Owin.Host.SystemWeb
- Microsoft.AspNet.Identity.Owin
Add the below code to Startup.Auth.cs which is under
App_Start folder. If such file is not found, then add the code which is under
ConfigureAuth method to your Startup.cs
The above code snippet will execute upon start of the API
project and which enables the bearer authentication to accept the tokens.
You can notice that,
- The endpoint URL to generate the token is /token
- Initialized the OAuth provider called ApplicationOAuthProvider and refresh token provider called ApplicationRefreshTokenProvider. We will talk about them more in coming section.
User Authentication:
Though we use the OWIN for token generation and
authorization, but we are going to have user authentication against our custom
database.
Typically, you can have a standard method anywhere in your
project to validate the user credentials. For demonstration purpose I am going
to have a method with name AuthenticateUserAgainstDB
under the Token generation section which describes below.
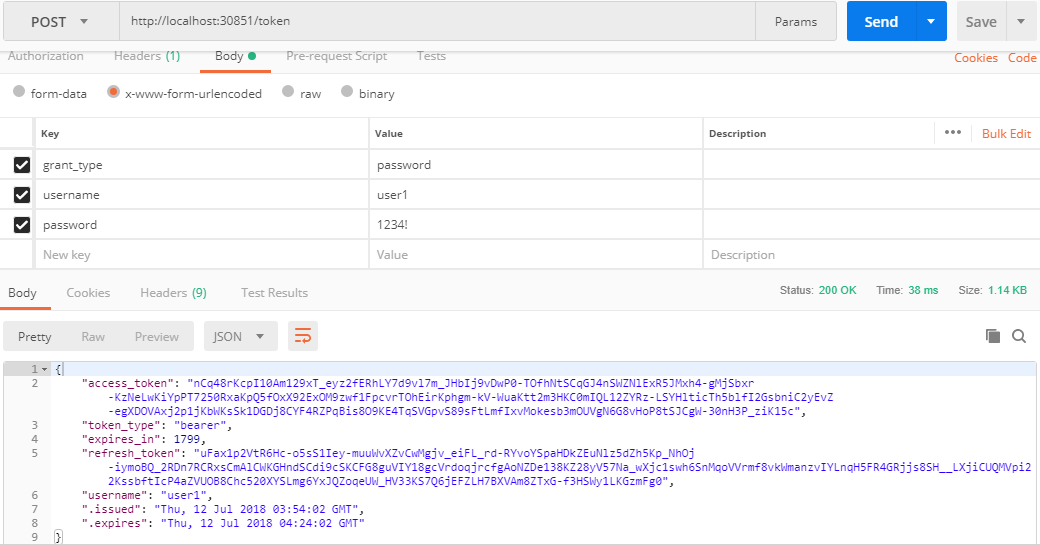
Token Generation:
For user authentication and generating the token, let us
have a provider called ApplicationOAuthProvider
which is the same provider told to OWIN in the above code.
The purpose of this provider is to validate the user against
the database (first method from below code) and generating the token (second
method in below code)
As mentioned in the token endpoint path under OWIN setup,
the URL to generate the token is,
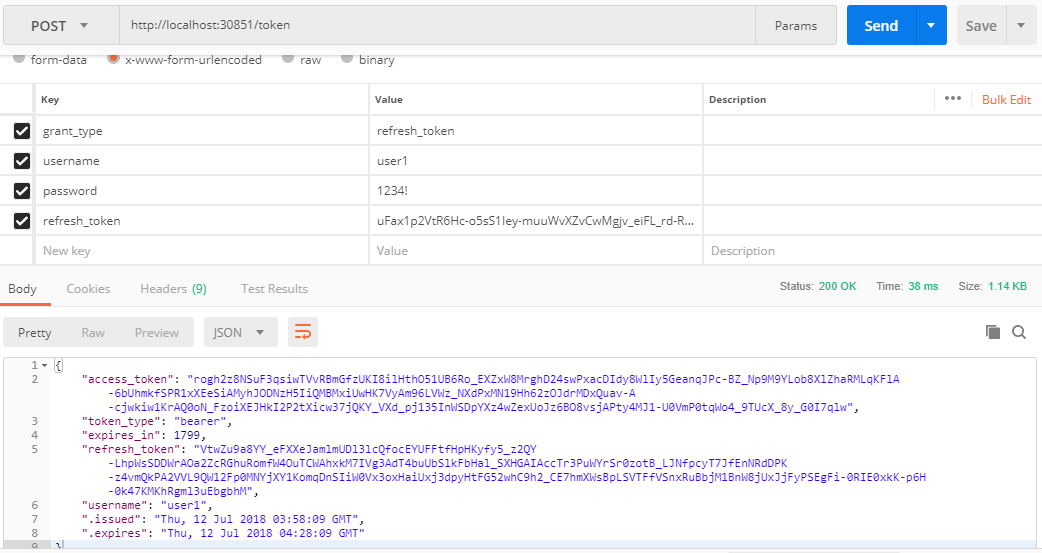
Refresh Token
Generation:
As shown in the above OWIN setup section, the validity of
the token is about 30 mins and after that the token is no more valid. If you
make any API calls with invalid token, you will end up with 401 Unauthorized error.
To generate the refresh token, let us have another provider
called ApplicationRefreshTokenProvider
which is the same one we passed to OWIN setup.
Generating the refresh token is also like the token
generation, except grand type and passing refresh token string which is part of
token generation response. The same token generation URL can be used to
generate the refresh token.
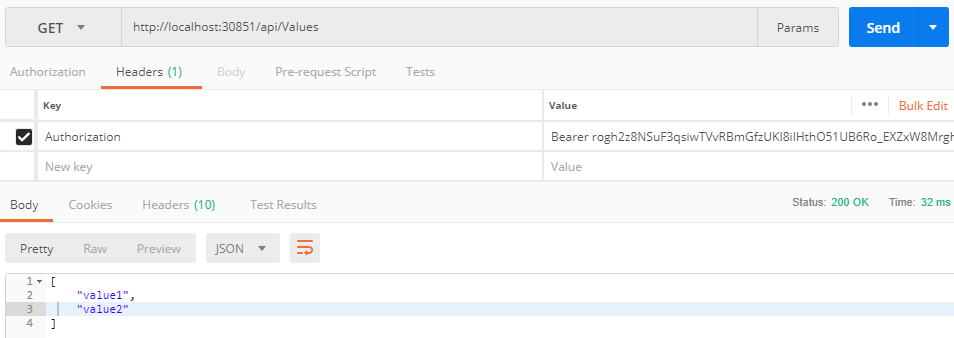
The methods which you don’t want to have anonymous access,
just mark them with [Authorize] attribute. If you would like to protect all the
methods in the controller, then mark the controller with [Authorize] attribute.
You must get supply the access token to each request to get
the response as shown below:
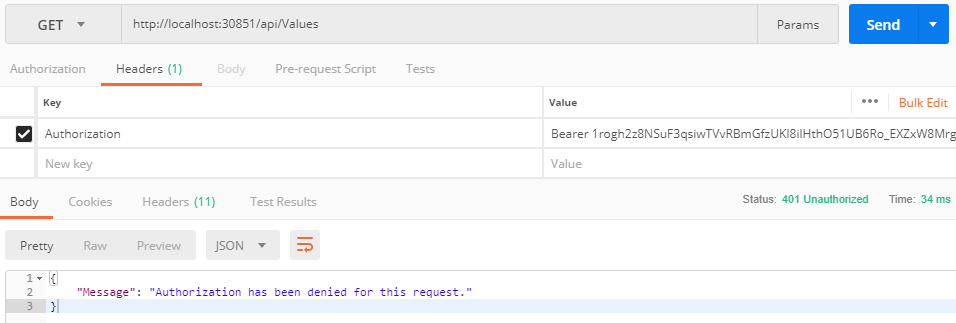
Your API requests will fail when your access token is
expired or invalid as shown below:
That’s all now what you need for securing Web APIs. I hope
it helps to you in a way you need.
Thank you for coming here and reading the article. Please
use the below comment box for any questions.










Nice keep it up.
ReplyDelete